API Transformation Bridge
Problem
Modern businesses rely on a plethora of systems, each playing a crucial role in the operation and success of the company. These systems are often disparate, having been created with their specific purpose in mind, using technologies and standards suitable for their individual tasks.
However, the effectiveness of these systems can be significantly hampered when they need to work together - especially when they're communicating data between each other. This is due to the fact that each system may have its own unique way of sending, receiving and interpreting data.
Take, for example, a scenario where System A needs to notify System B about some changes. System A may send updates in a form-encoded format while System B expects JSON. The incongruence in data format can lead to a communication breakdown, resulting in inefficiencies, data loss, and errors.
To make matters worse, the manual effort needed to transform data between different formats is labor-intensive, error-prone, and doesn't scale. So, how can we ensure seamless interoperability between different systems with diverse data formats?
Solution
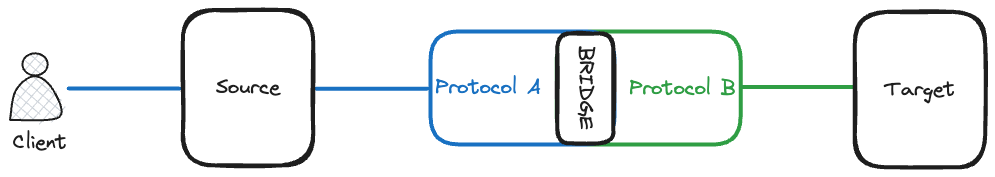
A solution to the problem lies in the implementation of an API Transformation Bridge. The Transformation Bridge acts as an intermediary between systems, effectively "translating" data formats and ensuring smooth and efficient communication.
To better understand the concept, let's examine a hypothetical use case:
-
User triggers an update in the Source System.
-
The Source System communicates this update to the Transformation Bridge API, using a standard protocol and authorization credentials.
-
The Transformation Bridge API processes this data, converting it from its original format to a more universal JSON structure. This conversion can be as simple as a straightforward encapsulation or a more complex transformation to match specific data requirements.
-
The Transformation Bridge API then sends this newly transformed JSON data to the Target System's Inbound Webhook, using the same authorization credentials as initially provided.
-
The Target System then accepts, processes, and stores this data. Once this is done, further actions can be executed as needed, leveraging the power of integrated systems.